ClevGuard Support: Monitor Devices with Others' Permission.
With our lives becoming more digitized, the security of our digital data is becoming a growing concern. Other than online data thefts, another unsettling thought for many is the possibility that someone has access to our computers and is monitoring all our activities. Whether it's our teammate, partner, or a malicious hacker, the thought that someone has access to the computer can make anyone feel uneasy.
If you are also concerned with this thought, then this article is for you. Here we will discuss how to know if someone has access to your computer, along with steps to protect your computer. So, let's get started!
In this article:
Part 1. How Can Someone Access Your Computer
There are multiple ways someone can use to access your computer. Some of the popular methods are listed below:
1 Use Computer Monitoring App
One common way people use to access someone's computer is by using a computer monitoring app. These apps are capable of tracking all computer activities, including access to all the files.
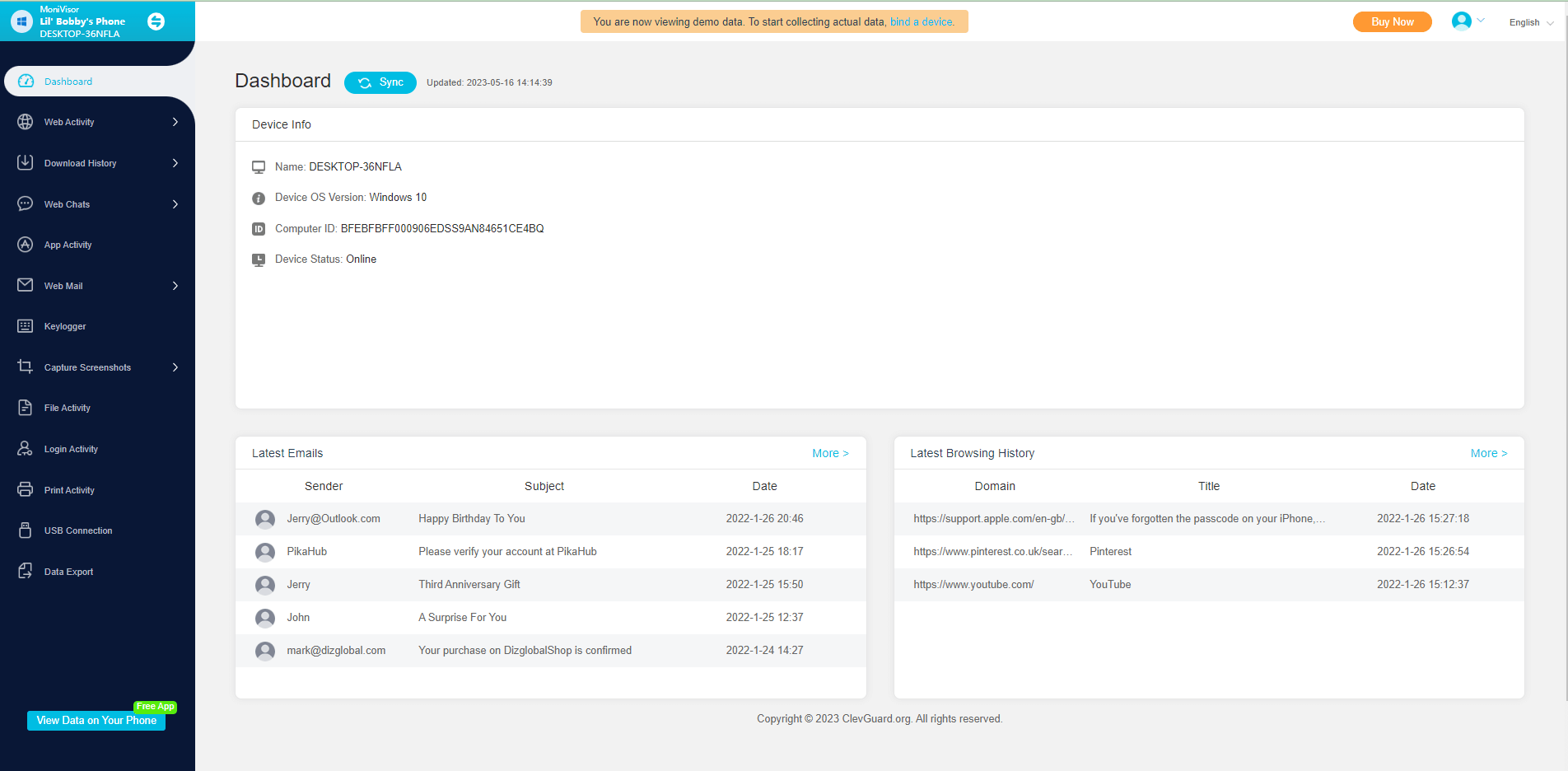
One popular computer monitoring app is MoniVisor for Win. It is the ultimate computer monitoring app that runs silently on the target computer and provides real-time access to all computer activities. It can monitor social media, track internet activity, read all emails, capture screenshots, view keystrokes typed, and many more. In short, MoniVisor for Win is an all-in-one, powerful monitoring app that can track all computer activities silently.

MoniVisor - Best PC Tracking Tool
- Screenshot PC acitivities silently
- Record every keystrokes
- Track web and app activities, file activities, login activities.
- View chat history of all the web chats and emails.
- Run in stealth mode and sync data in real-time.
Start Tracking Another Computer Right Now!
2 Physical Access
Physical access is another popular way of accessing someone's computer when the person is not around. This could be at the workplace, home, or any other location. Once someone gains access to your computer physically, they can access sensitive information, install malicious software, or do other damage.
3 Malware
Malicious software, or malware, is software that can exploit or harm a computer. Malware can enter your computer through different ways, such as a malicious website, email attachment, or software download. Once malware is installed in your computer, it can give hackers access to your computer, allowing them to control your computer remotely, install more software, or access sensitive data.

4 Network Access
If your computer is connected to a network, such as a local area network (LAN) or the internet, someone can access your computer through the network. This is possible if they get unauthorized network access or if they intercept data transmitted through the network. Once someone gains access to your computer through a network, they can access almost any data from your computer.
5 Phishing
Phishing is another cyberattack where hackers trick victims into providing sensitive information, such as usernames and passwords. Phishing attacks are often initiated through email, text, or social media messages. Once hackers have access to your sensitive information, they can use it to access your important data from the computer or even control the computer remotely.

Part 2. How to Know If Someone Has Access to Your Computer
Below are four checks on how to tell if someone has access to your computer:
1 Checking your Computer's Login History
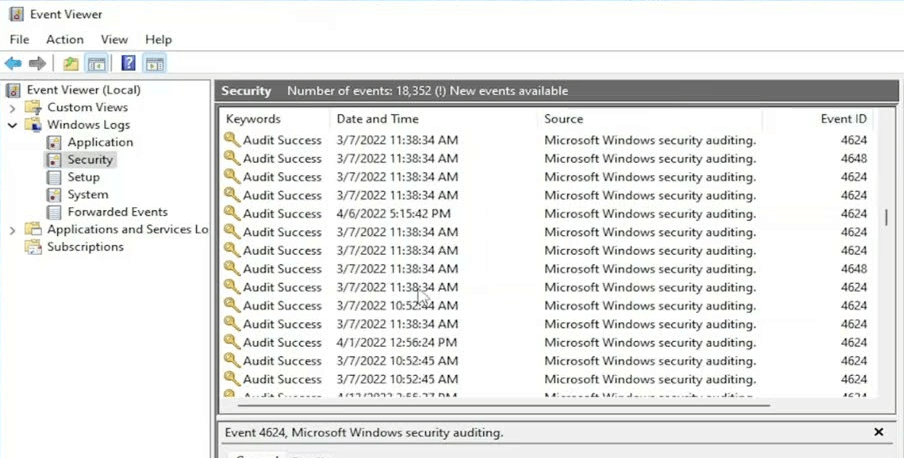
Checking your computer's login history is an effective way to check if someone has access to your computer. The login history provides detailed information about when someone has logged into your computer.
To access your login history on a Windows computer, go to the Event Viewer and navigate to Windows Log > Security. Look for logon events with an event ID of 4624, which indicate successful logon attempts. From there, if you see some suspicious login history outside your routine, then it can be an indication of outside access.
Another sign that someone has access to your computer is unusual computer behavior. If you suspect that files are modified, moved, or deleted without your knowledge or programs are opening and closing suddenly, it indicates unauthorized outside access.
2 Running a Malware Scan
If your computer is compromised with malware, then you can suspect some strange activities. For example, you can monitor your network activity and see if your internet connection is slower than usual or using more data than it should. Similarly, you might also experience that your computer is running slowly.
To check for any traces of malware, you should run a malware scan through a reputed antivirus software program. These programs can scan your computer thoroughly and detect and remove malware and suspicious files from your computer.
3 Reviewing your Security Settings
If someone has unauthorized access to your accounts, you may notice that your accounts have been logged in at unfamiliar times or locations, or you may receive a notification about a login attempt from a new device. So, reviewing your security settings is another way to determine if someone has access to your computer.
For Windows, go to Settings > Accounts. From there, you can check who can access your device and also check other settings. You can do similar checks from your Mac. In short, if you suspect some strange login attempts, then reviewing your security settings can help you find the root cause.
4 Checking for Remote Access Software
Remote access software allows hackers to access and control your computer remotely. If remote access software is installed on your computer, you might see suspicious pop-up messages or strange programs consuming more memory.
To check for remote access software on a Windows computer, go to "Add or remove programs" in the control panel to look for suspicious programs. Moreover, you can also check the "Task Manager" to see which software is running and consuming more memory.
Part 3. Steps to Take If Someone Has Access to Your Computer
If you suspect that someone has access to your computer, then below are some of the key steps you should take to protect your computer:
1 Secure your Accounts and Change Passwords
Once you suspect that someone has access to your computer, you should immediately secure your accounts by changing your passwords. Try to use b and unique passwords for each of your accounts, and avoid using the same password for all of your accounts.
For added security, it is also recommended to use two-factor authentication. Moreover, if you have some sensitive information stored on your computer, then try to move that data to a secure location, such as an encrypted USB drive.
2 Disconnect from the Internet
In most cases, hackers are able to access your computer remotely via the internet. So, once you suspect someone has access to your computer, immediately disconnect your computer from the internet. If you want to use the internet, try to use it from another device.
3 Remove Suspicious Programs and Files
If you are sure that someone has access to your computer remotely, then try to look for suspicious programs and files in your computer that are assisting the hacker in accessing your computer remotely. You can go to "Add or remove programs" in the control panel to look for suspicious programs. Alternatively, you can use reputed antivirus software to scan and remove such suspicious programs and files.

4 Contact Technical Support
If you find it difficult to secure your computer, you can contact technical support and ask them for assistance in securing your computer and preventing unauthorized access. If you have become a cyberattack victim, you can contact a cybersecurity professional or law enforcement for further assistance.
5 Take Measures to Prevent Future Unauthorized Access
It would be best if you also take measures to prevent future unauthorized access. To do that, you can take the below measures:
- Keep your operating systems and other installed apps up-to-date.
- Use reputed antivirus software and do regular scans.
- Avoid downloading software from untrusted sources.
- Open email attachments cautiously.
- Use b and unique passwords for all of your accounts.
In short, keep your security measures up-to-date to reduce the chances of unauthorized access in the future.
Conclusion
In this digitalized and tech-driven era, there are multiple ways someone can use to access your computer, such as through computer monitoring apps like MoniVisor for Win, physical access, network, malware, etc. Therefore, it is important to learn how to know if someone has access to your computer. Above, we have discussed some of the main signs that can tell if someone is accessing your computer, along with steps to take if someone has access to your computer. So, follow the above steps and protect your computer and privacy.







 Store
Store